Elevate your privileges with a registered application
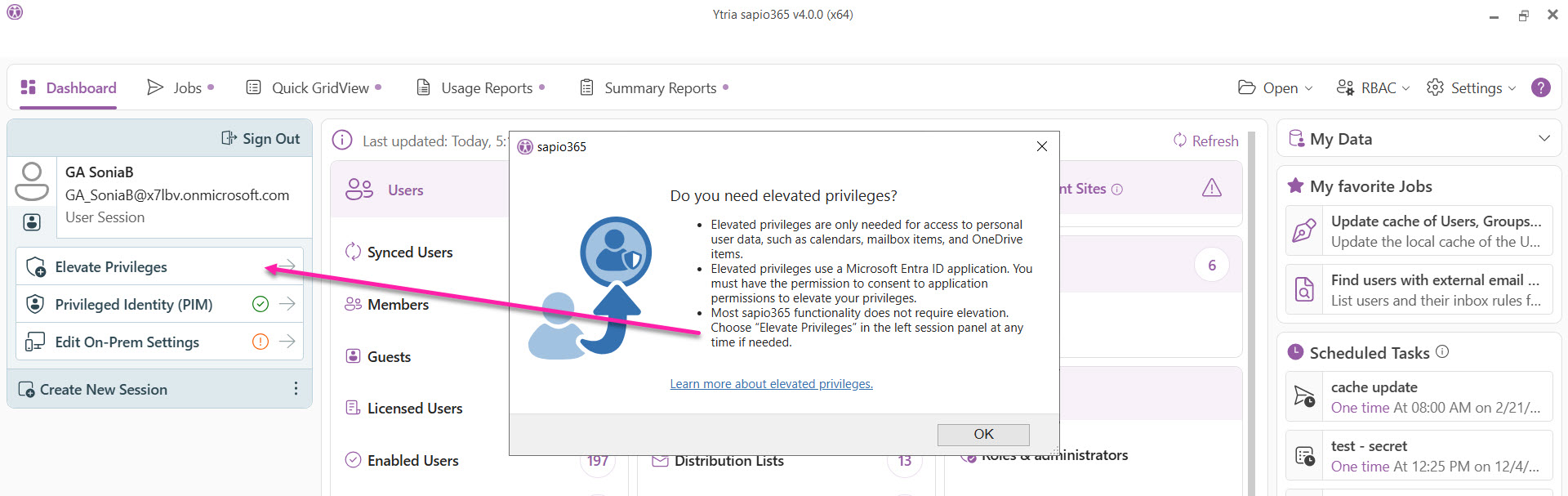
If you’re a global admin, sapio365 displays a notice when you sign in to start your session, letting you know that you can elevate your session and briefly explaining what elevated privileges involve. To proceed, simply click the Elevate Privileges button in the left panel.
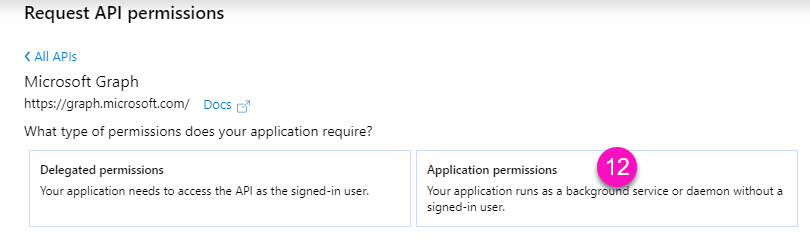
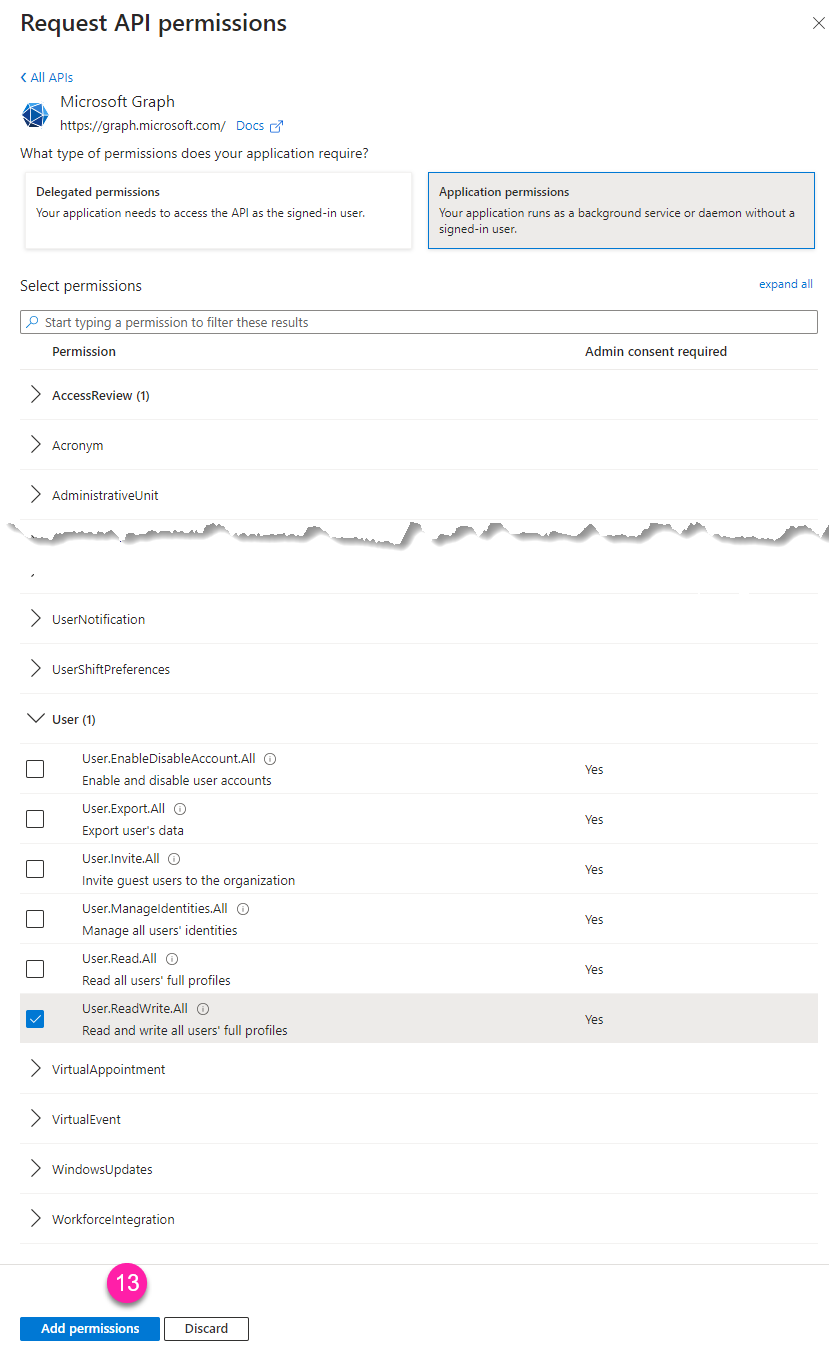
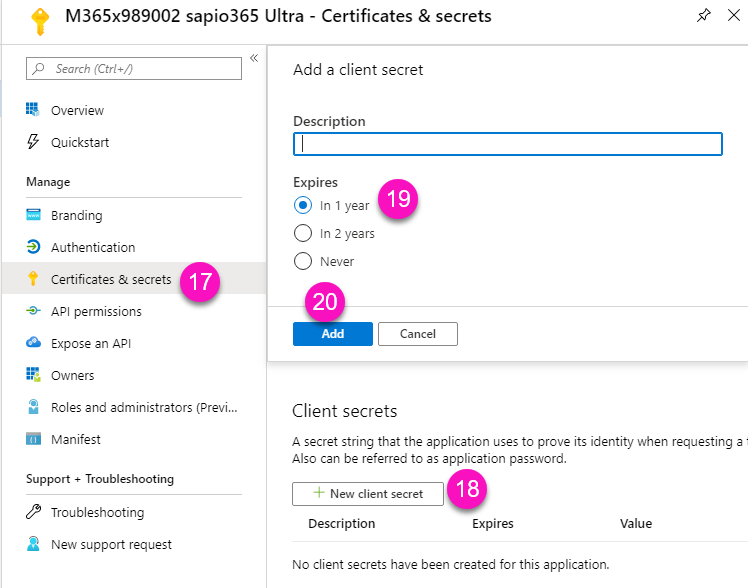
An elevated sapio365 session differs from a standard User session in two key ways. First, the registered application used for an elevated session does not require an interactive user sign-in. Second, while a regular User session uses a Ytria-provided application, an elevated session requires you to use a registered application in your own Entra tenant, configured with specific Microsoft Graph permission scopes and roles.
Requirements to elevate a sapio365 session
You must be a global admin or be assigned the sapio365 access role Can elevate a session.
Your tenant must allow creating a registered application that uses a client secret for authentication.
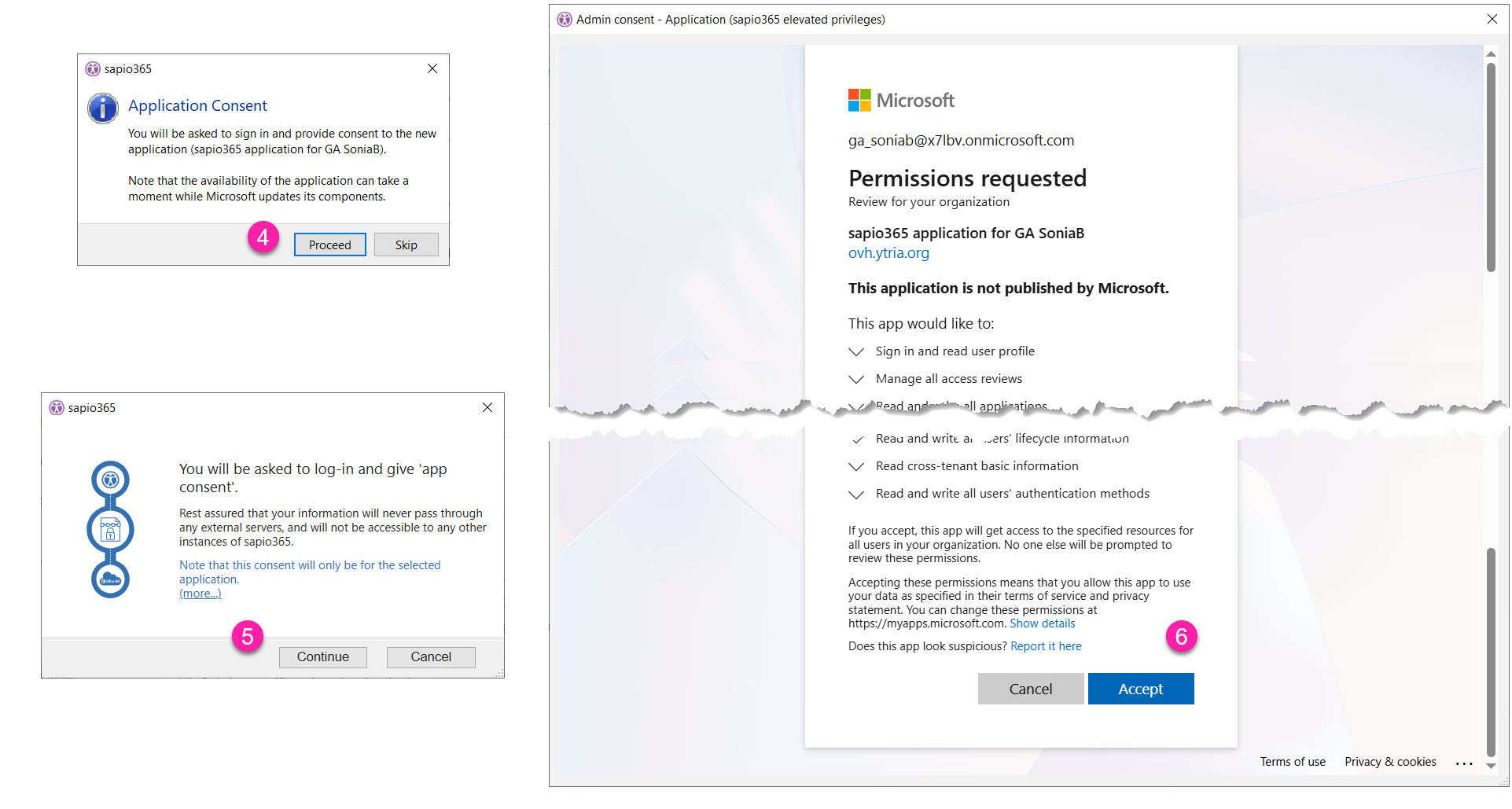
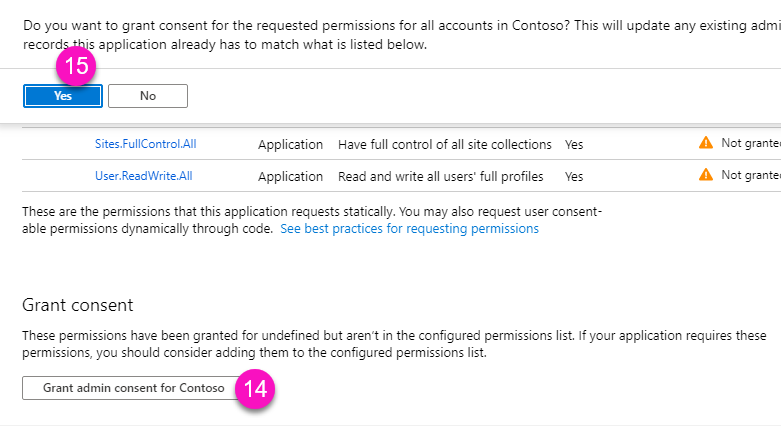
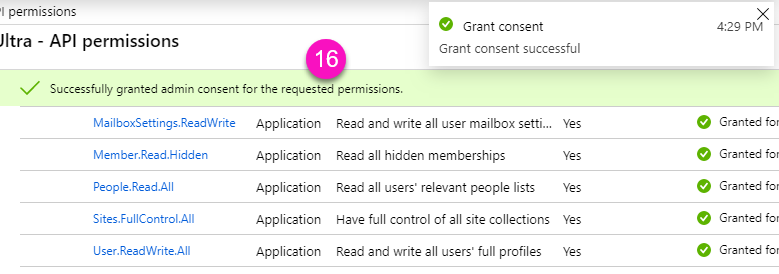
You must grant admin consent to the permissions required by this registered application.
How to elevate your sapio365 session
'CredentialTypeNotAllowedAsPerAppPolicy' error
If you encounter this error when creating a registered application, it may be caused by the Baseline security mode policy “Block new password credentials in apps.” Click here to troubleshoot.
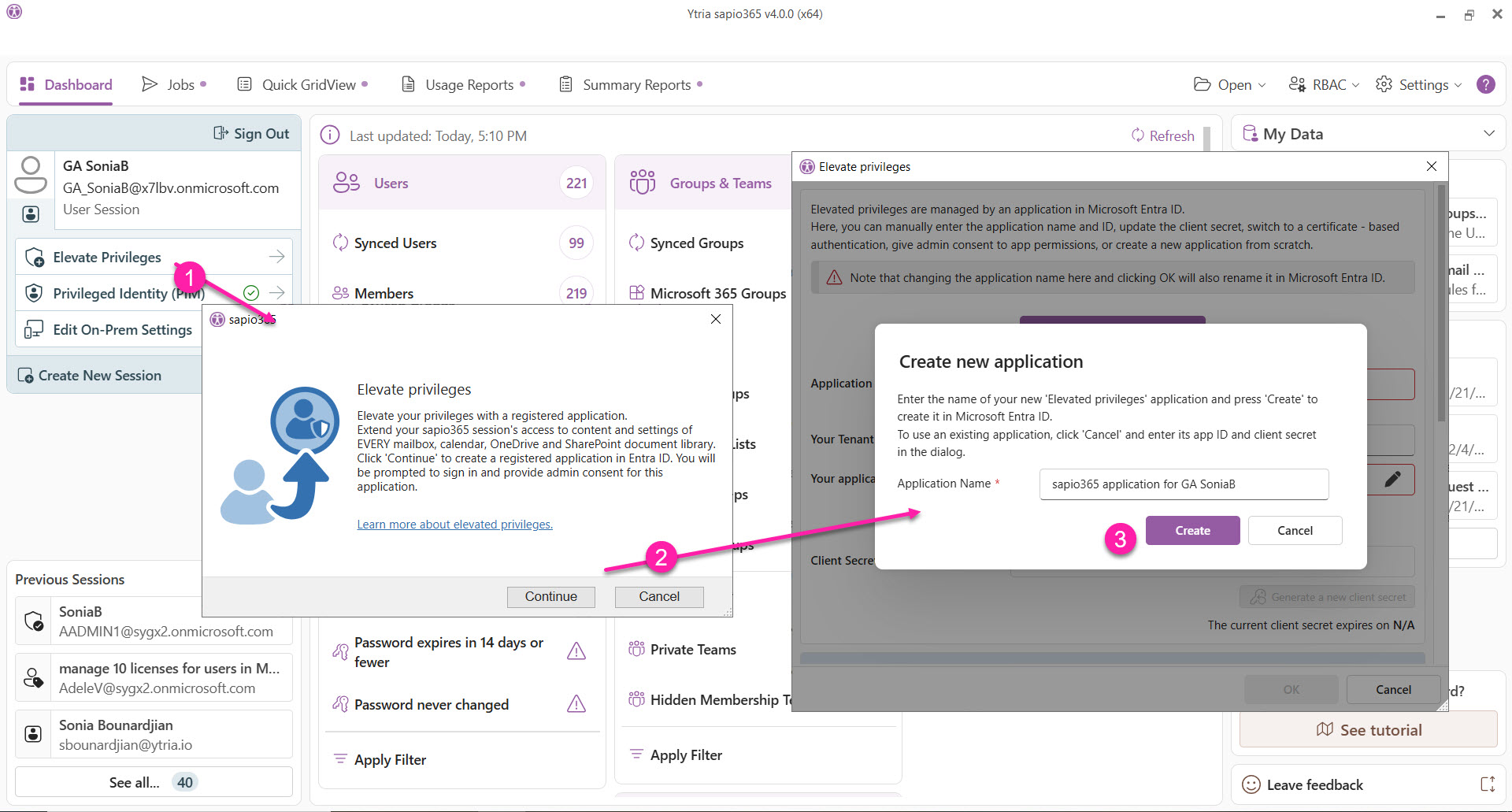
Click Elevate Privileges and follow the prompts to automatically create a registered app from sapio365.
See step-by-step instructions below.
What happens when you elevate your session
A dedicated registered application is created in Entra, and you’ll need to grant consent to its permissions.
Most actions made in Entra with an elevated sapio365 session are logged as the registered application.
A registered application is created when you:
Elevate a User session.
Create sapio365 RBAC credentials (see specific details in the sapio365 RBAC section).
For all three session types:
Most actions performed with an elevated sapio365 session are logged in Microsoft Entra ID as being executed by the sapio365 registered application (service principal).
Control and liability
Since there is no "user" signed in during a session with elevated privileges, there are real-life security implications that you should be aware of when setting up your application permissions.
Limit permissions of the “elevation application”
While sapio365 lets you automatically create and register the application yourself, you can modify the permission scopes for the application even after admin consent has been given. The permission scopes shown in this document represent the maximum access potential. You can decide for yourself any limits you'd like to place on your elevated session by removing permissions. You can create and register multiple applications, all with different permission profiles.
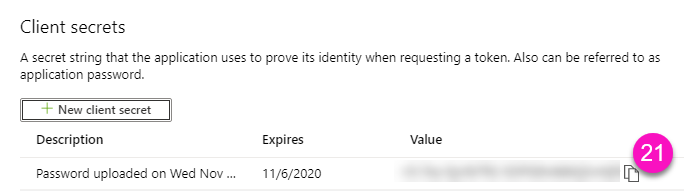
Application password/secret
Although the newly created password can be retrieved right after the creation of a registered application, it is not necessary to note it since you can reset it at any time from your sapio365 session or from Entra (registered applications).
Most actions in an elevated sapio365 session are executed by the registered application
To elevate a session, sapio365 will let you create an “elevation application” with “application type” permissions. Before sapio365 version 2.1.10, “delegated type” permissions from an elevated session were used to perform the majority of actions in sapio365. The “elevation application” was mainly used to handle users' mailbox and OneDrive content.
sapio365 2.1.10
With the release of 2.1.10, sapio365 now uses the “elevation application” to perform the majority of the actions. The “delegated type” permissions will only be used for some specific actions related to group management. This will ensure that elevating your session will effectively extend your capabilities.
sapio365 2.2.0
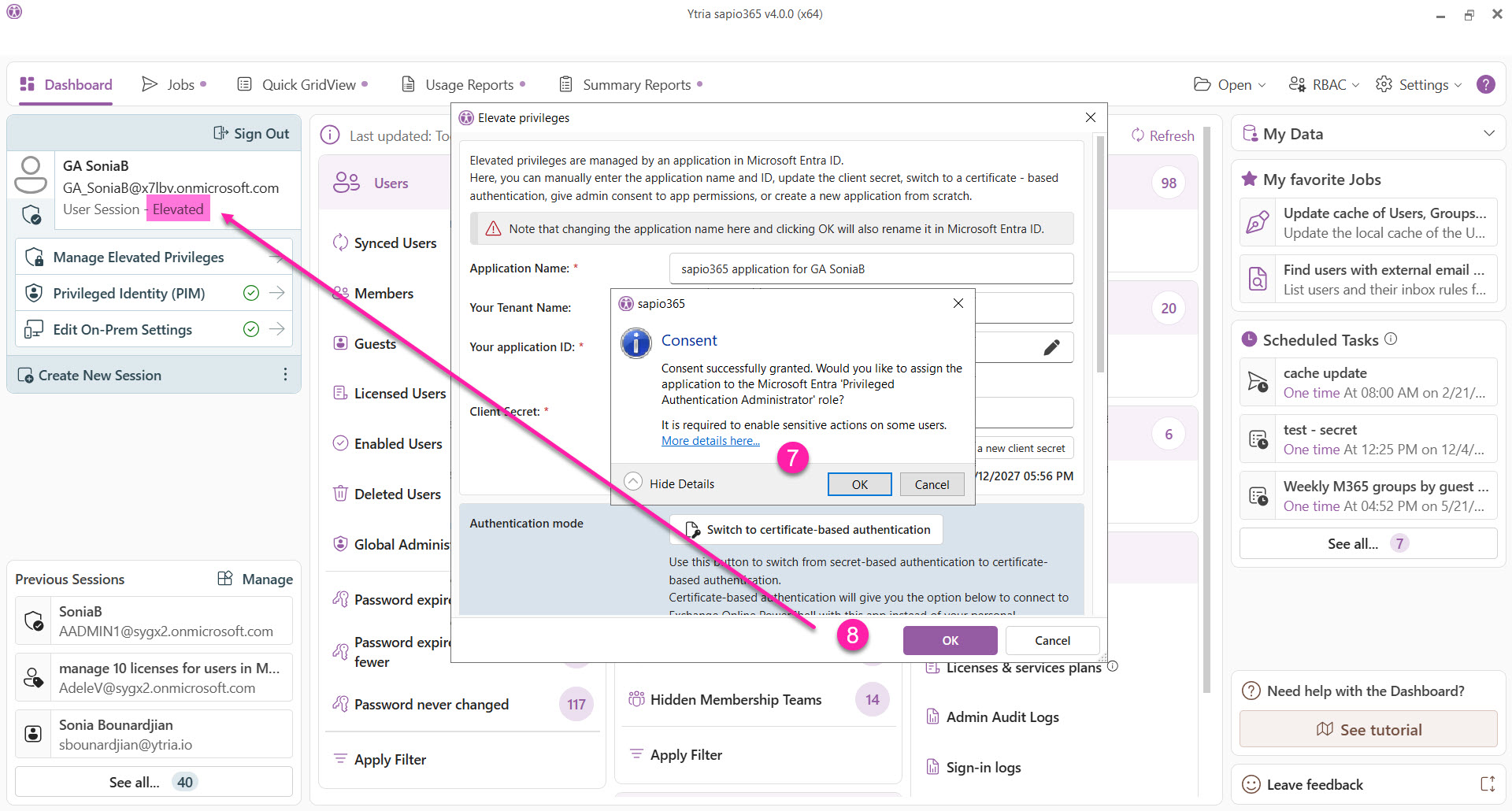
The 2.2.0 release takes into account deprecated Microsoft Graph API permissions. This resulted that some sensitive actions on certain users (ex. global admins) require the sapio365 registered application to have the 'Privileged Authentication Administrator' role assigned. During the app creation process you will have the option to assign the role to the app. This role assignment is necessary for the maximum functionality of sapio365 but it is not mandatory. See the full list of sensitive actions here.
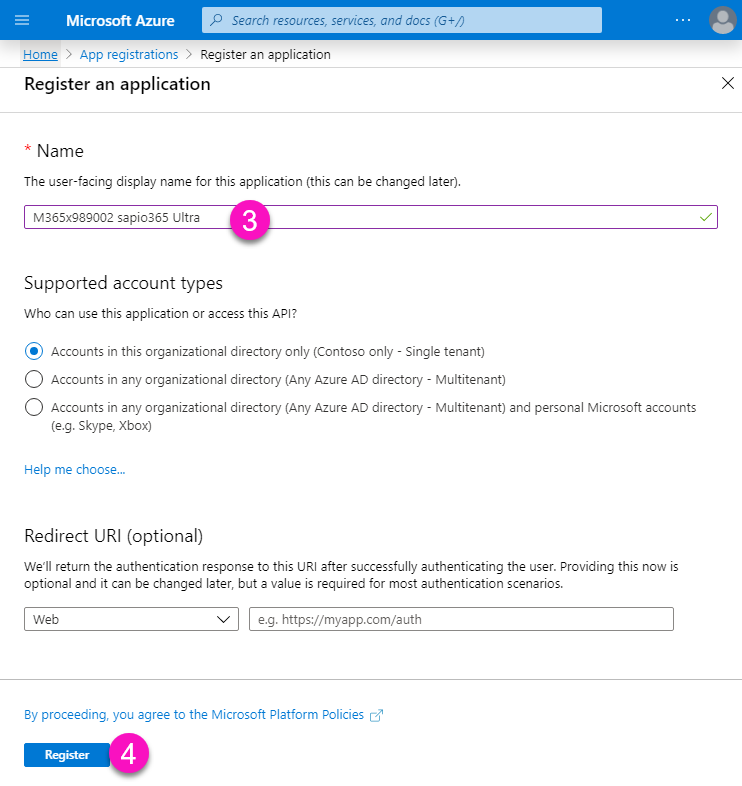
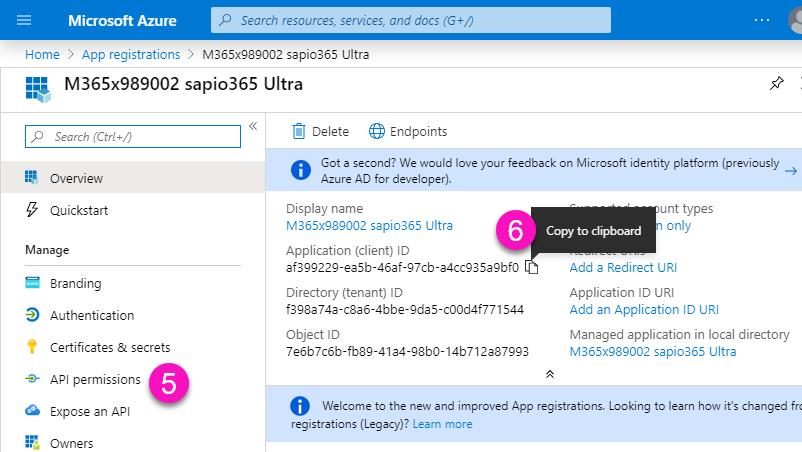
(Optional) Manually create application at the v2 Entra (Azure Active Directory) Endpoint
You have the option to manually create a registered application in Entra to elevate a sapio365 session. You'll need a key pair for proper authentication: an app ID that will identify the application and the password provided (see Step 8) which will authenticate the application.